Access Management: What is the IAAA Framework?
What is the access management IAAA framework? How does it work? What are some examples?
— Dusty

What is the IAAA Framework?
The IAAA("I triple-A") framework is a key cyber-security framework focused on access management, it stands for; Identity, Authentication, Authorisation and Accountability.
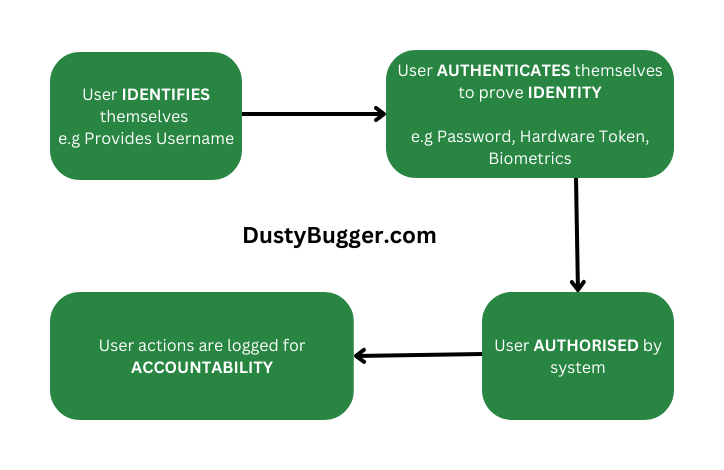
Let's take a look at each aspect:
Identity
Identity or Identification refers to a piece of information that distinguishes one entity from another. An entity could be anything from a person or a system process and their unique identities allow the system to track and monitor who or what processes are carrying out which tasks. A common form of identity is a username which is used in the authorisation process when you log in. Once logged in it is your username which can be used to track and identify your activity.
For Identification to work there must be:
- A system in place to create and assign unique identities for each entity.
- Entities must be forced to use this identity when accessing the system and not be allowed to share identities.
- Security must be applied on these identities.
Authentication
Authentication is the process of proving your identification. Authentication could take place in many different forms depending on the type of entity we are authenticating but a common method would be a user logging in with their username and password. It doesn't have to be a password though, there are multiple ways used to prove an identity based on these 4 key metrics:
- Something a user knows. (e.g Password)
- Something a user has. (e.g Hardware access token)
- Something a user is/does. (e.g Fingerprint, Retinal Scan, Voice recognition)
- Somewhere you are. (e.g Office, City, Country, Continent)
However just using a password, or any other authentication point on it's own, is no longer the acceptable standard. We now rely on Multi-Factor Authentication which uses a combination of 2 or more of these together. Each organisation will have its own set of authentication rules and requirements to prove an identity.
Often times you won't notice MFA being employed on the services you use on a daily basis because it is all satisfied in the background. For example, many organisations now employ location based authentication("Somewhere you are") using location, often derived from IP addresses, to prove your identification alongside your usual Password/Pin.
This can be seen when trying to access work accounts or trying to use your debit/credit card in another country, or while connected to an international VPN, and being met with blocked access.
As you can see Identity and Authentication are very closely linked, as without authenticating an identity the identity essentially becomes useless, and vice versa, without a unique identity to authenticate the authentication process proves nothing.
Authorisation
Authorisation is the policy that dictates access rights to assets and resources.
This happens once a user has authenticated their identity (e.g "Logging in"), in many systems the user will then be assigned an access token with their relevant "privileges" which will be checked every time they try to access an asset or resource to see if they are authorised to access the asset or resource in question.
Authorisation encompasses Access Control to enforce authorisation policies and there are multiple Access Control models that systems employ to manage this process such as:
- Discretionary Access Control (DAC): Managed by owner of the resource on an individual basis.
- Mandatory Access Control (MAC): Requires user clearance and file classification level to match.
- Role-Based Access Control (RBAC): Requires group based role to inherit access rights.
- Attribute-Based Access Control (ABAC): Requires a number of attributes to be met to gain access.
We plan to dedicate a full post to Procedural and People Security Controls in the future which will cover the Access Control models mentioned in more detail.
Accountability
Accountability is a form of Non-repudiation so we can prove and trace an action back to the individual entity responsible. This allows us to hold users accountable for their actions and deter malicious behaviour. How is this implemented?
Logging
Logging is used to make a record of actions and user info so that we can ensure accountability. These logs can be used to fall back on, to trace malicious behaviour within our network if preventative measures have failed.
Logs must record at minimum:
- Action that took place
- Entity responsible
- Time of action
Logs must remain backed up and secured so that they cannot be Edited, Deleted or Encrypted by attackers trying to hide their malicious activity or carry out a ransomware attack.