What is a VPN?
A VPN, is short for "Virtual Private Network", these allow you to create a secure network connection over a less secure public network. VPNs encrypt your internet traffic to make it challenging for third parties to track your online activities or steal your data.
VPNs are sometimes referred to as "tunnelling technologies" as they provide a secure encrypted tunnels through a less secure network.
How Does a VPN work?
Usually when you access the internet your traffic gets sent unencrypted from your device to your Internet Service Provider(ISP) who routes it to the destination across the internet. This exposes your personal home IP address and the destination address and a bunch of other data not only to your ISP, but to the sites you visit or any other prying eyes such as governments or hackers.
When using a Personal VPN, the VPN client installed on your device first encrypts your data and then sends it through your ISP to a remote server hosted by a VPN provider instead of directly to the destination address across internet. Only your device and the VPN provider has your encryption keys to be able to un-encrypt your data. Once your traffic has reached the remote server, the VPN server then acts as the source address when interacting across the internet.
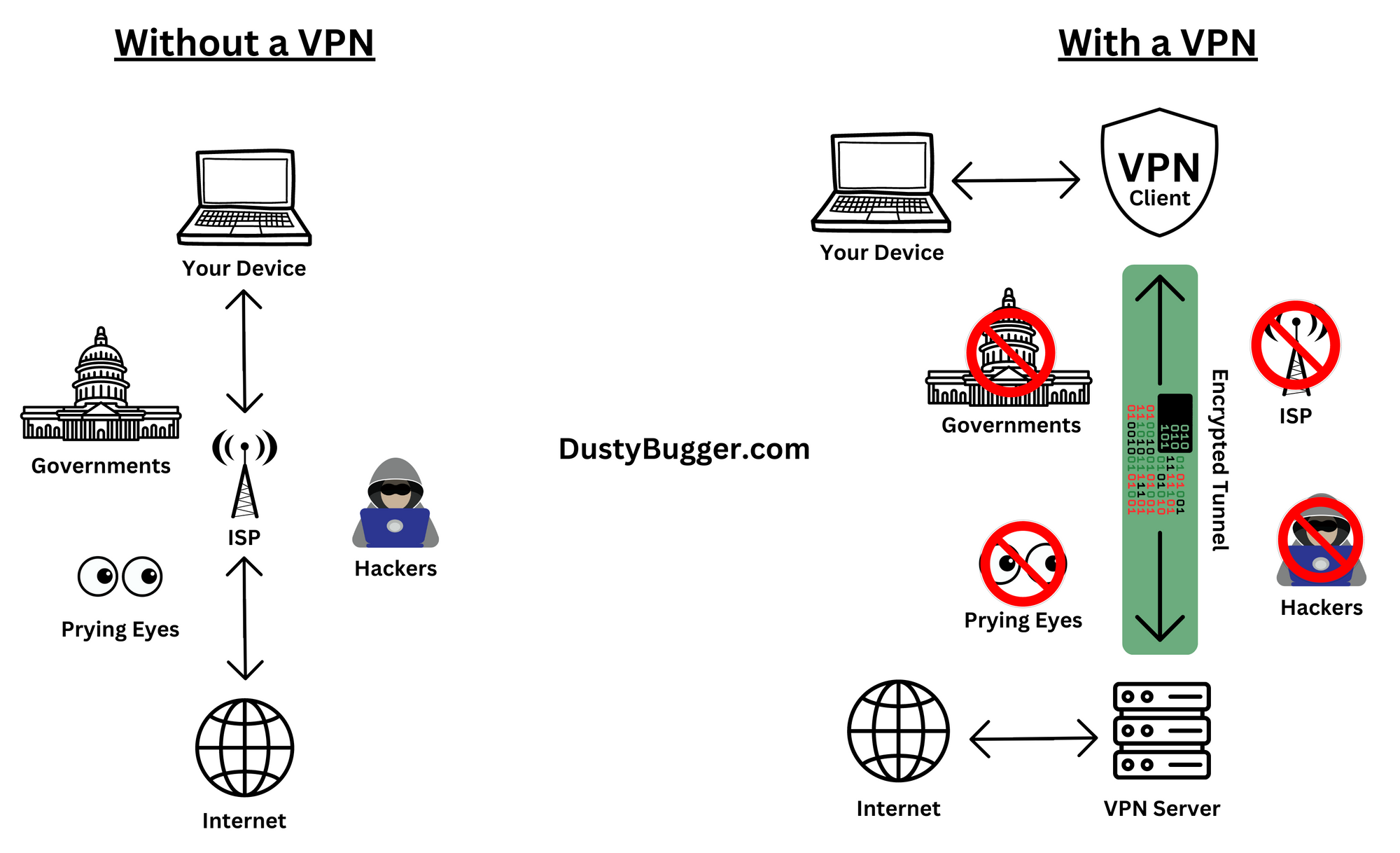
This means that while your Internet Service Provider(ISP) can see that your traffic is going to the VPN server, they cannot see the websites you are visiting or the data you send or recieve on the internet. Their view is obscured by the encryption and ends at the VPN server.
On the other side of the VPN server it also means that the websites you visit on the internet can only see the source of your traffic coming from the VPN server and not from your real IP address or location.
If any other prying eyes were to get their hands on your data, it would be useless as it is encrypted. This encryption provides:
- Confidentiality and Integrity of data - Encrypted data remains confidential and unchanged by third parties.
- Device authentication - Makes sure that the data is only coming from your device and only able to be decrypted by your VPN client or the VPN server.
- User authentication - Multi Factor Authentication to access the VPN client makes sure nobody can use your VPN service and impersonate you.
The most common protocol for VPN security is IPsec - Internet Protocol Security.
Benefits of a VPN
There multiple benefits of using a VPN such as:
- Privacy at home: As discussed above, ISPs can usually see and record all of your internet traffic. Using a VPN will provide you with privacy from your ISP, hackers, corporations and governments.
- Privacy on Public WIFI: Public WIFI connections can be incredibly dangerous and can be targeted by hackers. Since the public WIFI connections are open to everybody your data is at risk of being spied on and stolen by others connected to the network. Using a VPN will protect you from these threats.
- Censorship: Depending on your location, your local government may be censoring information. Using a VPN could help circumvent such restrictions.
- Blocked Websites: Depending on where you access the internet, organisations such as schools, businesses or public libraries may restrict access to certain websites. However using a VPN will encrypt your traffic and bypass such restrictions.
- Content Restrictions: If you're a regular user of streaming platforms such as Netflix, Youtube, Spotify or Amazon Prime you may have encountered the fact that a piece of content is not streamable to users in your country. Or maybe you've travelled abroad only to find out you can't continue watching your favourite show in your new location. Most VPN providers allow you to choose what geographical location your VPN connection travels to, giving you the ability to pick the locations where the content is able to be streamed to, therefore bypassing any restrictions.
Disadvantages of a VPN
- Slower speeds: When using a VPN your internet traffic isn't going directly to its destination and back to you. The extra steps involved in redirecting traffic to the VPN server could lead to a noticeable slowdown. However many VPN providers have had success in optimising their speeds so that you can perform high bandwidth activities such as streaming and gaming without issues.
- VPN blocks: Some websites and services across the internet may block IP addresses of known VPN Servers. However depending on your VPN client it should be super easy to generate a new session with a new IP address to try and get past these blocks.
- Stalker Cookies: While using a VPN you are provided privacy benefits mentioned above but some sites across the internet use tracking cookies to track you across the internet and identify who you are. So while a VPN does not protect you from these cookies it is easy enough to clear tracking cookies stored in your browser and even easier to use a private browser to stop these cookies automatically.
- Privacy, not Anonymity: It is important to note that privacy is not the same as anonymity. When using a VPN you will be provided with privacy from the parties mentioned above, but your VPN provider will still know who you are and be able to see your internet traffic as they are the ones acting as your proxy server.
- Only as Private as your VPN provider: Your VPN provider may keep logs of user activity and when put under pressure from entities such as the government and law enforcement, they may willingly give or be legally forced to hand over your data and activity records. There have also been cases of VPN providers claiming that they record no logs only to be later exposed of having given user info and logs to law enforcement.
So if you don't want to put your trust in VPN providers and are looking for anonymity rather than just privacy, your best bet would be the TOR browser. A full post is coming on TOR and the Dark web soon!
Subscribe to our newsletter to be notified:
Common VPN Models used within Organisations
There are three common VPN models used within organisations:
- Remote Access
- Site-to-Site (Intranet)
- Site-to-Site (Extranet)
1. What is a Remote Access VPN?
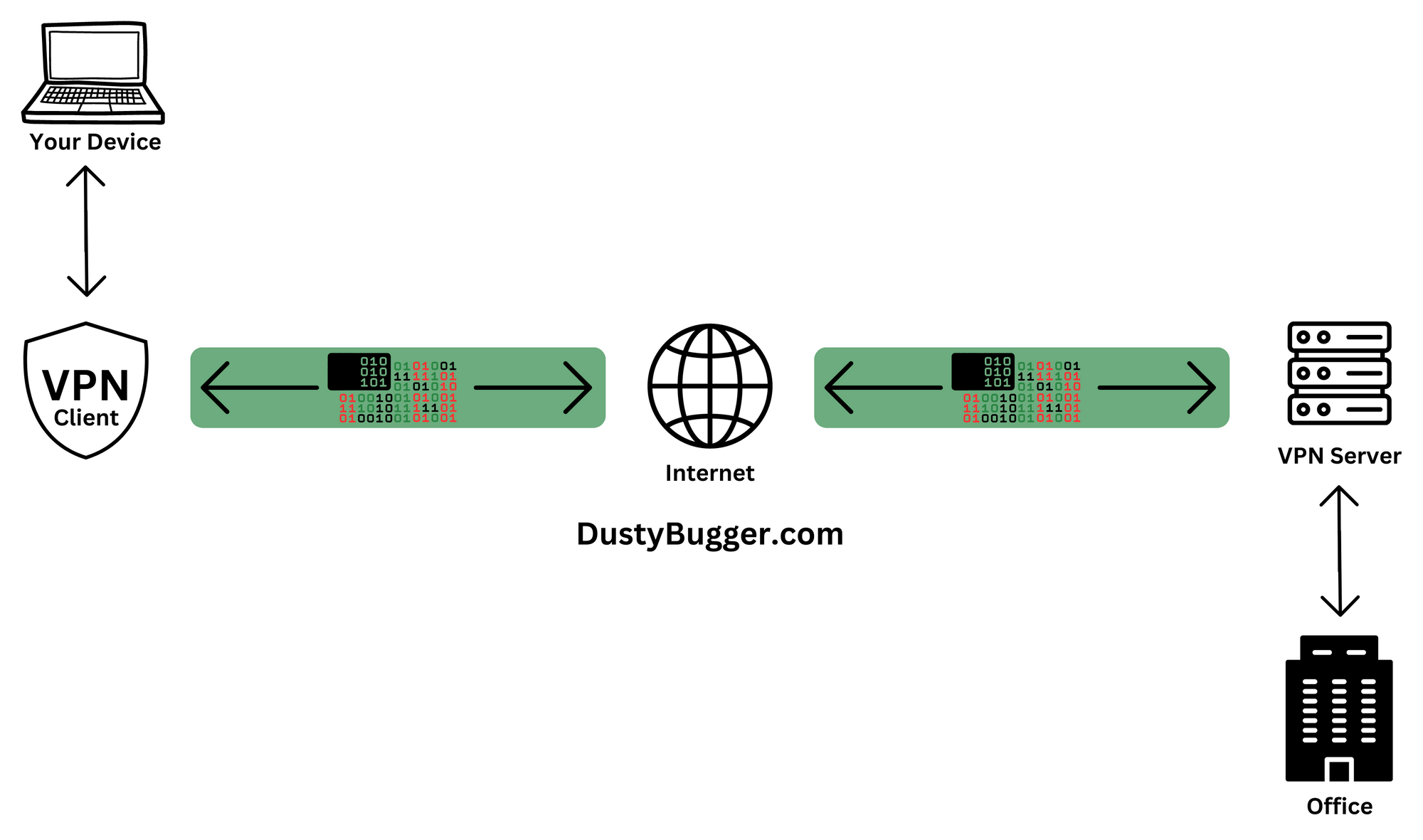
The first type is a Remote Access VPN, also know as a Client-Server VPN, typically used by remote employees. In this model, the employee's work device already has the VPN client installed and configured and when the employee supplies their access credentials they get secure access to the network remotely.
This is the most similar to the set up of VPNs for personal use and privacy mentioned earlier, except that instead of using the encrypted connection to the VPN server to privately browse the internet, it is being used to remotely access a specific private network.
2. What is an Intranet Site-to-Site VPN?
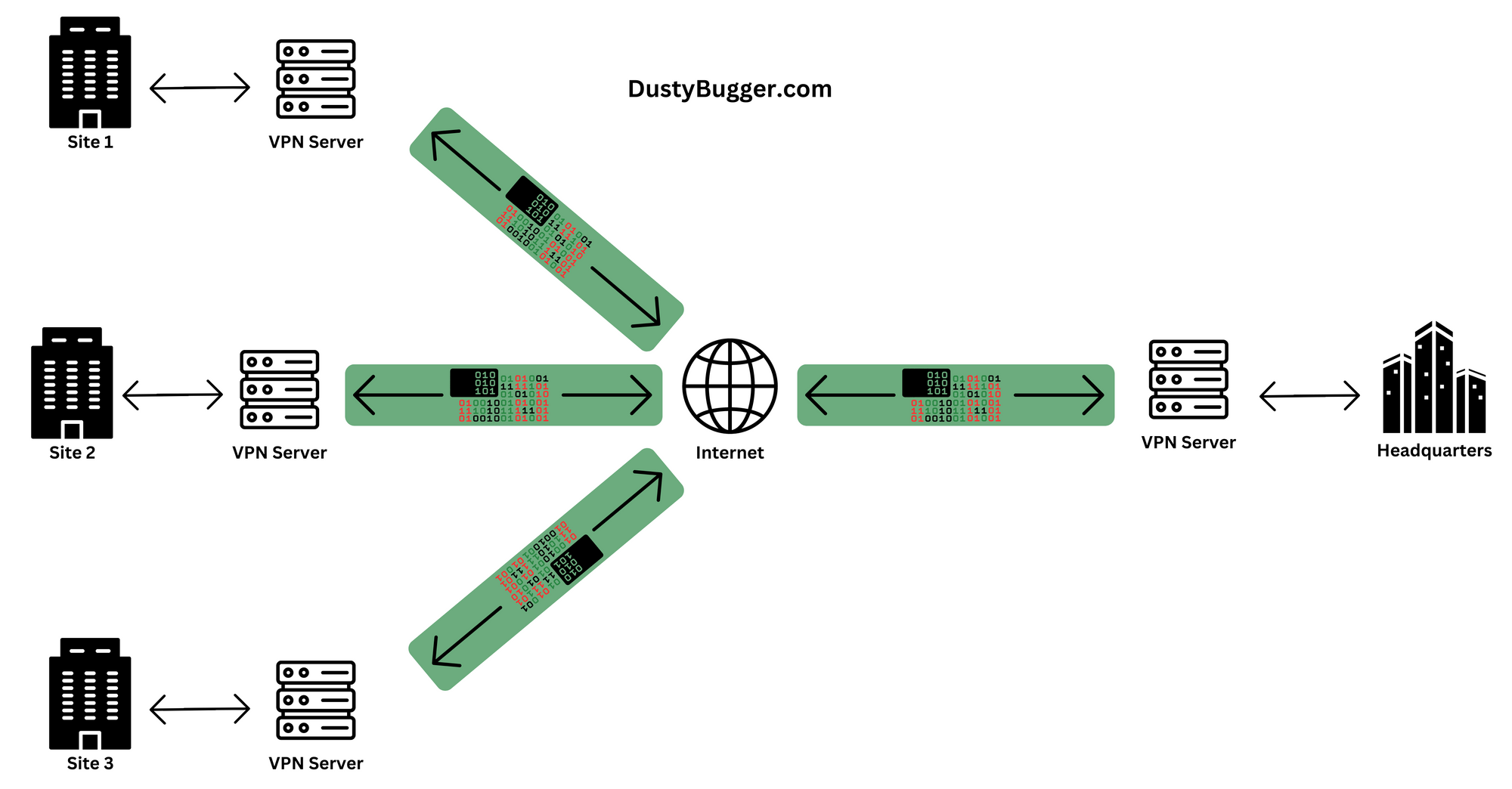
Another common type of VPN is an intranet that is used to connect different sites within an organisation. This is called a Site-to-Site VPN as it creates a closed network where each site can connect with each other.
This VPN could be over a public network, like the internet, or another network where the data needs to be isolated from other traffic.
In this model there is a VPN gateway/server at each location that is setup to send and receive to and from gateways at other locations. Before any data leaves each site, it passes through the gateway which uses a VPN protocol such as IPsec to encrypt the traffic, which is then only decrypted at the destination gateway.
3. What is an Extranet Site-to-Site VPN?
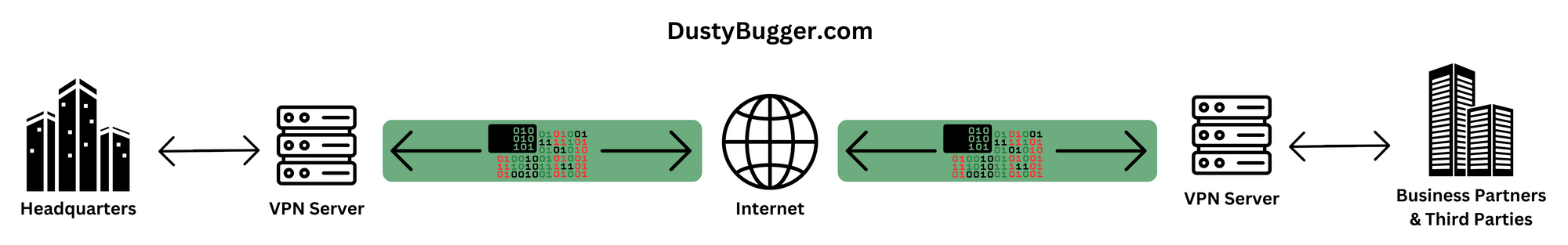
This type of VPN works the same as the Intranet Site-to-Site VPN mentioned above, however the use case and implementation are slightly different. While an intranet VPN serves as a secure connection to other locations within the same organisation, an extranet VPN serves as a secure connection to locations outside of the organisation, aka, a connection between two different Intranets.
The extranet is the part of the organisation's network that is made available to trusted Partners & Third Parties. This allows easy sharing of resources, data and services for business purposes but also allows the organisation to control and limit access to resources, data and services the third parties can access.
Be careful not to mistake this with a Demilitarised Zone, as these extranet VPNs are only available to authorised parties and are not open to the public.
Conclusion
A VPN can provide a secure connection between you and the internet. Using a VPN will send your data through an encrypted tunnel to the VPN server which then acts as your proxy server. This allows you to privately access the internet without exposing your real location and IP address.
A VPN can also be used to access any other network in a secure manner. This could be in the form of Remote Access, Internal Site-to-Site, or External Site-to-Site connections with Third Parties.
VPN Recommendations:
We recommend ProtonVPN:


