The cybersecurity landscape is filled with various types of attackers, each with unique motivations, skill levels, and available resources. To protect yourself and your assets in this environment, it's crucial to understand who your enemies are, how they will attack, and what motivates them.
What Are Threat Actors?
A threat actor is any individual or group that is responsible for, or likely to, carry out malicious actions against another individual, group, system or asset. These can range from inexperienced troublemakers to well-funded government agencies.
It is important to be able to characterise these threat actors by their attributes and motivations so that we can identify their re-appearance across multiple isolated incidents and better plan for how to defend against them.
Types of Threat Actors
In the world of Cyber-Security the lines between different types of threat actors can often be blurred, however there are a few key groups that you should be aware of:
Nation-State
Nation State actors can either be direct government agencies or government-sponsored hacking groups that are working on behalf of a country. Their operations are typically large-scale, highly sophisticated, and deeply resourced.
They're often involved in cyber espionage, critical infrastructure attacks, or disruption during conflicts. Examples would include Russia’s “Fancy Bear” or China’s “APT41”.
Unskilled Attacker ("Script Kiddies")
Script Kiddies are low-level attackers with limited skills in the field of hacking or awareness of the potential consequences. They often rely on pre-written malicious tools or scripts found online, with little understanding of how they work. Their attacks are usually unsophisticated and noisy (e.g. DDOS attacks), but they can still cause a lot of harm.
A good example would be the 17-year-old boy who was responsible for the TalkTalk 2015 cyber attack.
Hacktivist
Hacktivism is a blend of hacking and activism. Therefore, hacktivists are politically or socially motivated attackers. Their goal isn’t financial (usually), as they care more about making a statement or disrupting systems they disagree with. Common hacktivism attacks include website defacements and denial-of-service (DoS) attacks.
A well-known example of a hacktivist group would be Anonymous, who are a decentralised collective known for its operations against various governments, corporations, and organisations. Their notable acts of hacktivism include:
- Project Chanology (2008): A campaign against the Church of Scientology, which included DDoS attacks, prank calls, and protests.
- Operation Tunisia (2011): Support for Tunisian protests during the Arab Spring by attacking government websites to promote democracy.
Insider Threat
As the name suggests, an insider threat is when the attacker (or potential attacker) is someone within the organisation, usually an employee, contractor, or partner. These types of threats are particularly dangerous as the attackers already have authorised access to the organisation, which makes proactive prevention or detection difficult. Additionally, their motivations can vary widely. Some might be motivated by revenge, financial gain, or even coercion by external actors.
A good example of an insider threat would be Edward Snowden, who was a former contractor for the National Security Agency (NSA). Snowden was motivated by his conscience and desire to 'do the right thing' by exposing numerous NSA and international government agency mass surveillance programs.
Organised Crime
Organised cybercrime involves highly sophisticated groups of professional criminals that are motivated primarily by financial gain. These actors operate like a professional business and consist of highly skilled individuals who specialise in different aspects of hacking operations. These groups are often well-funded and international in scope, allowing them to procure the best hacking talent and tools money can buy, making the group highly effective and very dangerous.
A prime example of organised cyber-crime is the Carbanak Group. They are said to be responsible for the theft of over a billion dollars from financial institutions worldwide.
Shadow IT
Shadow IT refers to information technology systems and solutions built and used within an organisation without explicit organisational approval or oversight. These setups are often created by employees looking to circumvent internal IT roadblocks, seeking user-friendly, efficient, or innovative solutions that may not be supported in their organisation. Individuals engaging in shadow IT might leverage cloud services or other unapproved technologies to fulfill their needs, often leading to security and compliance risks due to inadequate oversight and integration with official systems.
The threat actors responsible for Shadow IT systems do not usually fit the traditional definition of an "attacker", as their intentions are usually not malicious. However, they still pose a major risk as their actions may unknowingly expose the organisation to vulnerabilities.
An example of shadow IT can be seen in the case of Dropbox’s early days. Employees at various companies started using Dropbox for file storage and sharing due to its ease of use, without explicit approval from their IT departments. While not malicious, this kind of shadow IT activity posed significant security risks, as sensitive company data was stored in an unmonitored external cloud environment, potentially accessible by unauthorised parties.
Attributes of Threat Actors
Threat actors can have their attributes broken down into at least 3 key areas:
1. Location
The "location" of a threat actor refers to their access to the target of their malicious activities. This is usually categorised as either Internal or External, however it can be broken down further to describe this access in detail. Such as whether an external party is part of a trusted supply chain, or whether an internal party is a full time employee or a 3rd party employee with internal access to the premises (e.g. Janitor, Repair-man, etc).
The key differentiator is that internal actors have legitimate access, while external actors must "break in".
2. Resources/Funding
The resources and funding available to threat actors significantly affect their capacity to plan and execute cyber attacks. These attributes determine the scope, scale, and persistence of their operations. Well-funded actors, such as nation-state groups or organised cyber criminals, can afford advanced tools, training, and talent, leading to more sophisticated, high-impact attacks. They might invest in zero-day exploits, custom malware, or long-term cyber espionage campaigns.
In contrast, threat actors with limited resources, like script kiddies or some individual hacktivists, often utilise readily available tools or scripts, resulting in less sophisticated and opportunistic attacks. This disparity in funding influences not only the types of attacks threat actors can carry out but also their ability to adapt and respond to defensive measures.
3. Sophistication/Capabilities
The sophistication and capabilities of a threat actor refer to their technical skill level, strategic planning abilities, and access to advanced tools or tactics. These factors dictate how effectively they can carry out their objectives.
High-sophistication actors, such as nation-state or organised crime groups, often employ custom-built malware, exploit zero-day vulnerabilities, and use multi-stage attacks that evade detection for extended periods. These groups tend to follow structured methodologies, often mirroring the kind of planning you’d expect from a military operation.
On the other hand, low-sophistication attackers might rely on basic phishing attacks, automated tools, or public exploits downloaded from the internet. These attacks are often noisy, easily detected, and typically fail against basic security controls. However, even low-capability actors can be dangerous if they target vulnerable systems with little protection.
Motivations Behind Cyber Attacks
While understanding who the attacker is matters, understanding why they attack is equally critical. Common motivations of threat actors can be seen below:
- Data Exfiltration - Stealing sensitive data like customer info, trade secrets, or health records. Often to either leak, sell, or to create chain-attacks.
- Espionage - Typically done by nation-states. Involves spying to gain an advantage (political, military, or economic).
- Service Disruption - Often used by hacktivists or nation-states to cause downtime in critical services (think DDoS attacks).
- Blackmail - Seen in ransomware attacks where data is encrypted and a payment is demanded. Sensitive data capture by hackers could also be used to blackmail/coerce targets for political and philosophical causes.
- Financial Gain - This is the most common motivation - achieved by stealing money directly, demanding ransoms or selling data on the dark web.
- Philosophical or Political Beliefs - Tied to hacktivism. Attacks are used to contribute to or protest against certain causes, organisations and governments.
- Ethical - Often carried by threat actors who believe they are doing the right thing according to their own personal ethics. E.g. Edward Snowden. However this motivation can materialise in many different types of threat actors.
- Revenge - Often seen in insider threats - a disgruntled employee causes harm after being reprimanded or fired.
- Disruption / Chaos - While nation-states may cause disruption as part of a broader strategic campaign. Some attackers want to cause chaos and “watch the world burn” for its own sake. These attacks can be very unpredictable and irrational.
- War - Cyber warfare tactics that disable infrastructure, manipulate public perception, or sabotage enemy operations are very useful in times of military conflict.
Threat Actor Visual Breakdown
I have put together the table below to visually breakdown each threat actor and their corresponding attributes and motivations:
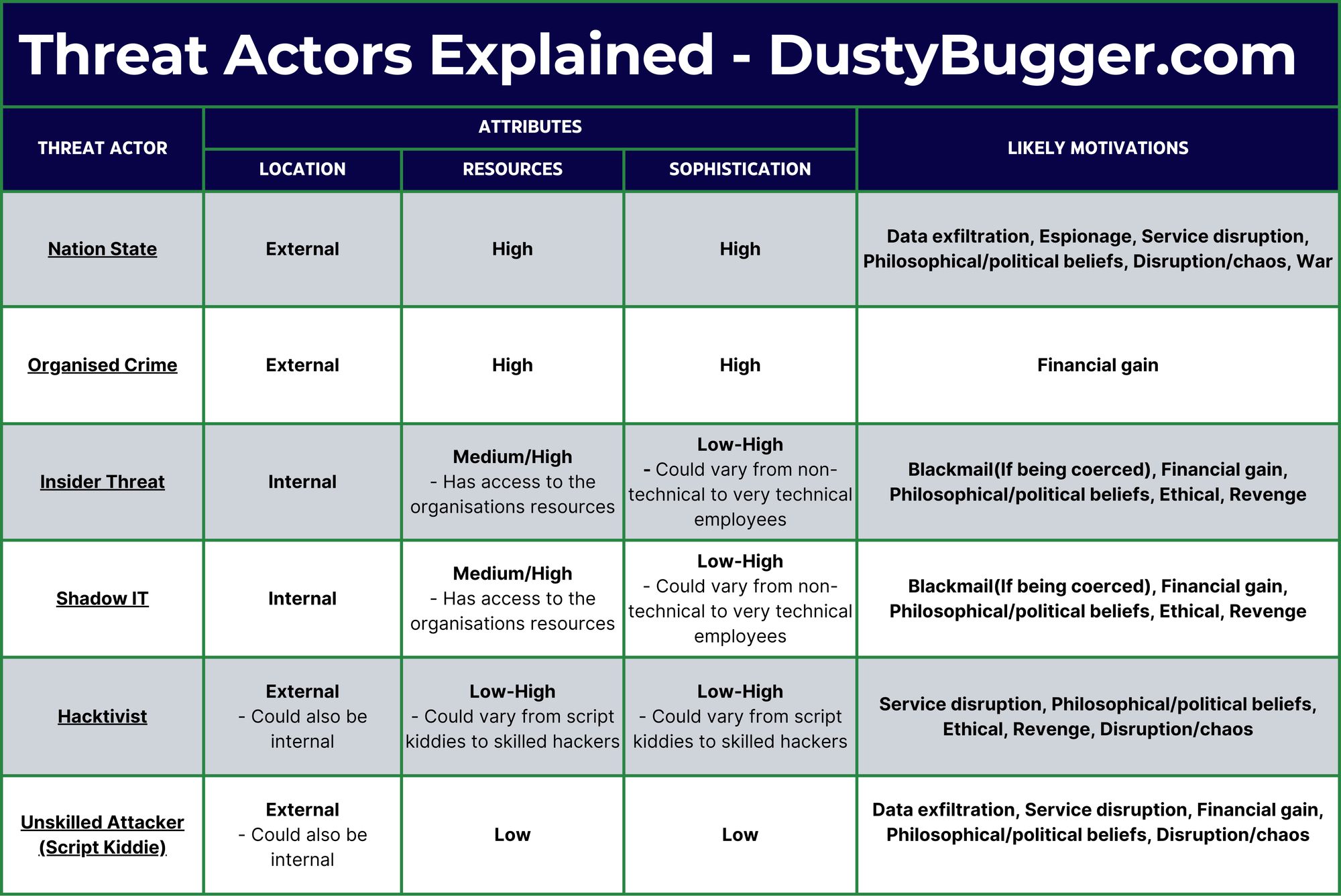
As you can see, threat actors can come in many form with varying attributes. By recognising these types, attributes, and motivations, you’ll be better prepared to defend your systems, tailor your response plans, and ultimately stay ahead of their next move.
