Defence-In-Depth: The Onion Model
What is Defence-In-Depth? What are the Layers of Defence? How is it implemented? What is Defence-In-Breadth? What is The Human Layer?
— Dusty

What is Defence-In-Depth?
In an increasingly interconnected and digital world, ensuring robust cyber-security measures is of paramount importance. Cyber-criminals are becoming more sophisticated, and their attacks can have severe consequences for individuals, businesses, and even entire nations. One approach that has gained widespread recognition and adoption is Defence-In-Depth.
Defence-In-Depth, aka Security-In-Depth, is a cyber-security strategy that involves implementing multiple layers of security to decrease vulnerabilities and contain threats. This approach is designed in hopes that even if one layer of security is breached, the other layers will still be able to protect the organisation's assets.
As well as being called Security-In-Depth this strategy is sometimes also referred to as the "Onion model" due to an onion having many layers or the "Swiss Cheese model", explained by the holes in a slice of swiss cheese representing a vulnerability that an attacker can pass through only to be met and stopped by the next layer of "cheese".
The Layers of Defence
A successful Defence-In-Depth strategy involves the implementation of multiple security layers from physical security all the way to data security that collectively form a comprehensive cyber-security framework.
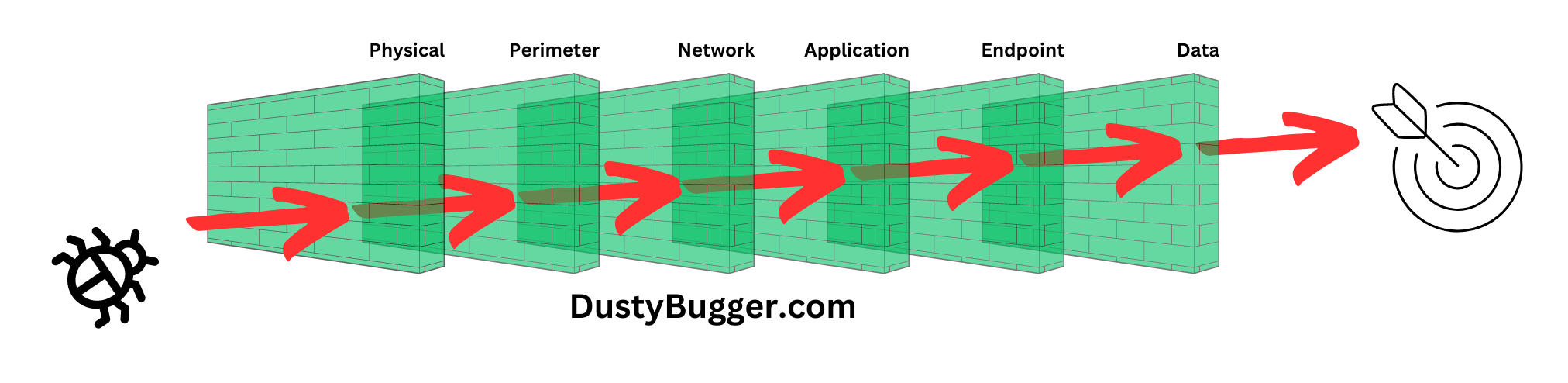
Let's explore these layers in detail:
Physical Defence
Physical defence forms the first line of defence for organisations with physical assets and infrastructure. Physical security measures include fences/walls, gates, surveillance cameras, alarm systems, secure facility design, and security personnel. These measures aim to prevent unauthorised physical access to critical systems, data centres, or restricted areas. By integrating physical defence with the upcoming digital security layers, organisations create a comprehensive Defence-In-Depth strategy that addresses both digital and physical vulnerabilities and attack vectors.
Perimeter Security
Perimeter Security is a subsection of network security and forms the first line of digital defence by safeguarding the perimeter of an organisation's network. It involves securing entry and exit points to the network by deploying technologies such as Firewalls, Demilitarised zones (DMZs), Intrusion Detection and Prevention Systems and Denial of Service protection.
Network Security
Network security encompasses a broader set of measures aimed at protecting the entire network rather than just the perimeter. However as they are both essentially considered network security, the objectives and technologies used will overlap so it is hard to define exactly where one ends and the other begins. Lets take a look at a few examples of what network security implements outside of the perimeter technologies mentioned above:
- Network segmentation: Segmentation is implemented to stop attacks spreading across the entire network.
- Secure Wi-Fi: Wi-Fi networks require specific security measures to protect against unauthorised access and eavesdropping. Implementing strong authentication mechanisms and encryption protocols and regularly updating Wi-Fi access points with security patches help secure wireless networks.
- Network Encryption: Network encryption protects data in transit by encrypting communication between network devices. Secure protocols like Transport Layer Security (TLS) or Internet Protocol Security (IPsec) can be employed to secure network traffic and ensure the confidentiality and integrity of data.
- Network Device Hardening: Network security involves implementing proper configurations and security measures on network devices such as routers, switches, and firewalls. This includes disabling unnecessary services, enforcing strong passwords, updating firmware regularly, and implementing access control lists (ACLs) to control traffic flow.
These are just a few examples but by implementing such network security measures in addition to perimeter security, organisations can establish a robust defence against a wide range of cyber threats and be confident in the overall security of their network.
Application Security
Application security involves securing the software and applications used within an organisation. It encompasses secure coding practices, web application firewalls, vulnerability scanning and testing, and the implementation of a secure software development lifecycle (SDLC). It also employs the AAA framework which we have a dedicated post on, but it stands for:
- Authentication: Used to verify the identity of a person.
- Authorisation: Used to verify a person has the correct permissions to access resources.
- Accounting: Used to record a persons access by logging their activities.
Endpoint Security
Endpoints, such as Servers, Laptops, Desktops, and Mobile devices, are often targeted by cyber-criminals as footholds into the network. Endpoint security measures include deploying anti-malware and antivirus solutions, host-based firewalls, endpoint detection and response (EDR) systems, device encryption, and effective patch management.
Data Security
Data is a valuable asset that requires stringent protection. Data security measures involve processes such as Data Classification and Access Policies, Encryption of data at rest and in transport, and Cryptographic key management. Implementing data loss prevention (DLP) solutions helps prevent sensitive data from being leaked or misused. Additionally, regular backup and disaster recovery processes ensure data availability and minimise the impact of potential breaches.
Defence-In-Breadth
Defence-In-Breadth is a newer term compared to Defence-In-Depth due to the fact that the size of organisations and their subsequent systems and infrastructure have rapidly grown in recent years and will only continue to do so.
The complexity of these modern networks is astounding and it becomes even more complex when you consider the connections to suppliers, partners, remote workers and much more.
We must now give just as much focus to Breadth as we do Depth, as no matter how many security layers you apply to 99% of your estate, you are still only as secure as the 1% that is overlooked and left vulnerable.
With the size of modern organisations spanning all across the globe with thousands if not tens-of-thousands(or more...), devices and sites in their IT estate it is only more likely for more and more of those devices to be overlooked, untracked and left vulnerable. This is why having an IT management system that allows you to track and have clear view of any and all devices and their current status and security posture is so valuable.
The Human Layer - Security Awareness Training
No cyber-security strategy is complete without addressing the human factor. Security awareness training programmes must be carried out regularly to educate and remind employees about Acceptable use, Current best practice(e.g password hygiene and reporting suspicious activity), and potential threats(e.g Phishing and other Social engineering attacks).
Human error is often found to be a major cause in many data breaches so by implementing a regular Security Awareness and Training programme for all employees organisations can significantly reduce the risk of human error causing such breaches.
Continuous Improvement and Adaptation
Cyber-security is an rapidly evolving field, and organisations must continuously improve their defences. Regular security audits and assessments are needed to identify gaps in existing security measures and Penetration testing will help identify vulnerabilities before malicious actors can exploit them.
Conclusion
Defence-In-Depth and In-Breadth is an essential approach to cyber-security, providing organisations with a multi-layered defence across their entire estate against evolving threats. By combining Physical, Perimeter, Network, Application, Endpoint and Data security, with an added emphasis on the human element with Security Awareness Training, organisations can significantly enhance their cyber resilience.