1.4 - Public Key Infrastructure (PKI)

Learning Objectives
Explain the importance of using appropriate cryptographic solutions.
- Public Key Infrastructure (PKI)
- Public key
- Private key
- Key escrow
Public Key Infrastructure (PKI)
Public Key Infrastructure (PKI) is a very broad term that refers to a general framework that encompasses the policies, procedures, hardware and software involved in managing public key encryption and digital certificates. The purpose of PKI is to create, distribute, manage and store these public keys and digital certificates, ensuring secure communication over insecure networks like the internet.
Although the concept may seem straightforward, implementing PKI can be a complex task, even for small organisations. It requires thorough planning and decision-making regarding the encryption methods and standards to be used. PKI also plays a crucial role in binding public keys and certificates to individuals or devices, typically with the help of a Certificate Authority (CA). This process ensures that entities, whether people or devices, can be trusted and verified as authentic in digital interactions.
Public Key Cryptography
Public key cryptography refers to a type of asymmetric encryption that uses two keys, one to encrypt and the other to decrypt data.
Key generation for public key cryptography involves creating both keys simultaneously. This process requires a high degree of randomisation and involves complex mathematical calculations, often including large prime numbers for certain algorithms. This process ensures that the two keys are unique and the mathematical relationship between the two keys ensures data encrypted with the public key can only be decrypted by the corresponding private key. Lets take a look at each type of key:
Public Key
The public key is one half of the cryptographic key pair used in asymmetric encryption, the other half is the private key which we will discuss in a moment. The public key can be shared openly with anyone, without any risk, as it can only be used to encrypt data. Only the corresponding private key can decrypt the encrypted data.
Although the public and private keys are mathematically related, it’s impossible to derive one from the other—there’s no way to reverse-engineer the private key from the public key. This allows anyone to use the public key to encrypt data and as long as you keep your private key secure, only you can decrypt the data, even if someone intercepts the encrypted message.
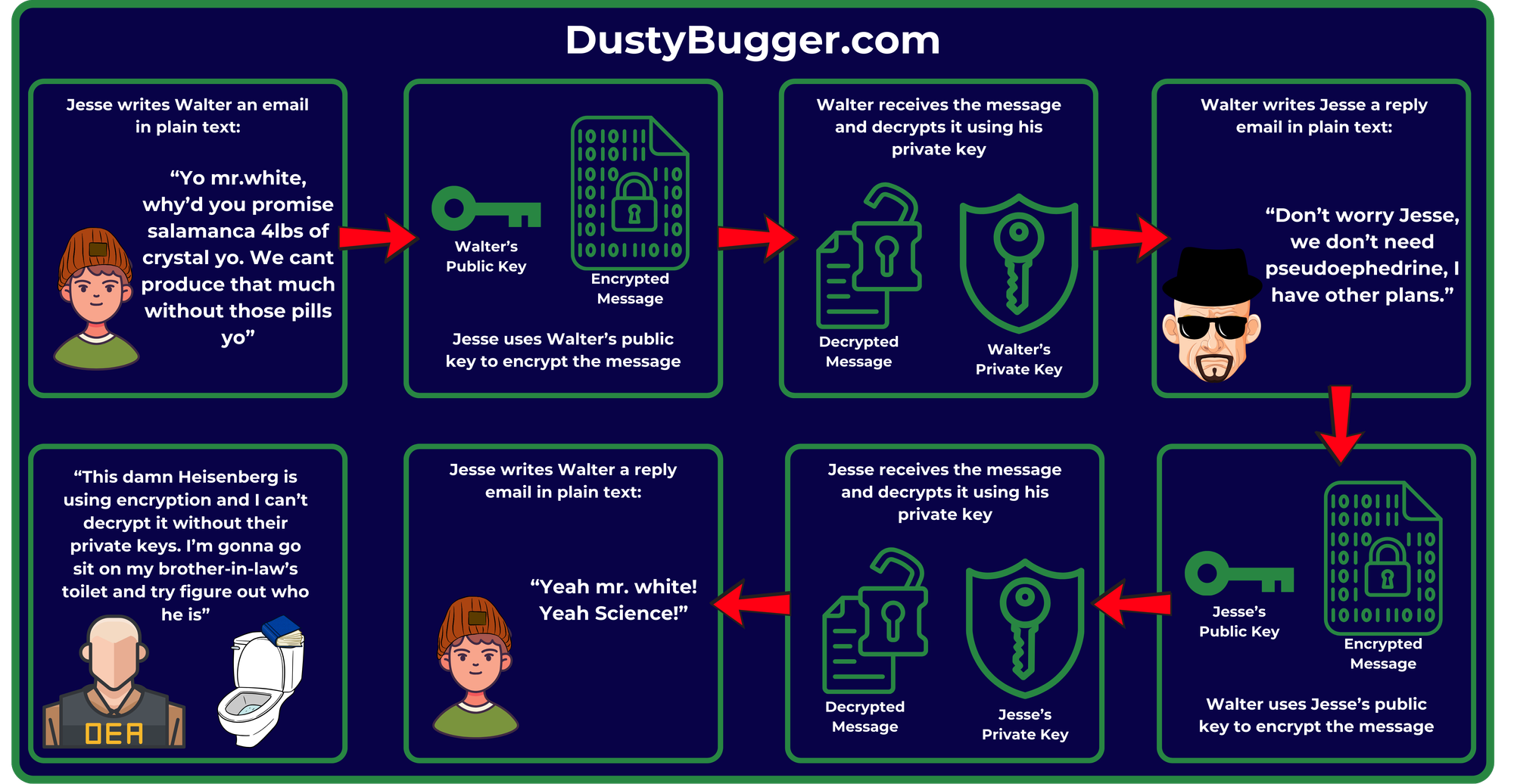
Example: When Jesse wants to send Walter an encrypted message without the DEA being able to read it, he uses Walter’s public key to encrypt the message before sending it. Now only Walters’s private key can decrypt it, ensuring that only he can read the message.
Private Key
The private key is the second part of the cryptographic key pair and is kept secret by its owner. It’s used to decrypt data that has been encrypted with the corresponding public key and is also used to sign data, creating digital signatures for authentication. (Digital Signatures will be covered in detail in a later lesson.)
Example: Walter receives the encrypted message from Jesse and uses his private key to decrypt it. If Walter wants to reply to Jesse he would use Jesse's public key to encrypt the reply message so that only Jesse can decrypt it with his own private key.
The public and private key pair in PKI enables secure communication and authentication between parties, forming the backbone of secure communications in applications like email, websites (HTTPS), and virtual private networks (VPNs).
Key Escrow
When you're dealing with a single person it is easy for both of you to share public keys and manage your own private keys. However, in a large organisation with thousands of employees who have their own public-private key pair, it quickly becomes too much information to manage.
Key escrow is a mechanism where a trusted third party holds copies of private keys or other sensitive cryptographic material until you need to access them. This allows for keys to be used and stored conveniently, be recovered if they are lost, or for 'easy compliance' in cases where law enforcement/government agencies need access to encrypted data for lawful purposes...
- Why Key Escrow Matters: While encryption can ensure privacy and security, key escrow provides a safeguard in case users lose access to their keys. In enterprise environments, key escrow can ensure business continuity even when employees who held critical keys are no longer with the company.
- Key Escrow Controversy: Key escrow is a double-edged sword. While it can be useful for key recovery, it also creates a potential vulnerability. If the escrow agent is compromised, the keys stored there could be misused to expose sensitive data.
Handing over your private key to a third party may sound like terrible operational security, but in a business environment it may be required to ensure uptime and smooth work flows without losing of access to critical data.
Real-World Examples of PKI Use
- Secure Email Communication (S/MIME): PKI enables users to send encrypted and digitally signed emails using asymmetric encryption. This ensures that the email content can only be read by the intended recipient and that the recipient can verify the sender’s identity.
- Secure Websites (HTTPS ): When you visit a website with HTTPS, PKI is working behind the scenes. The website has a digital certificate issued by a certificate authority (CA) to prove its identity. This certificate contains the public key that your browser uses to encrypt your data so that only the websites server can decrypt it with their private key. This ensures the confidentiality and integrity of the data being exchanged.
- Virtual Private Networks (VPNs): Many VPNs rely on PKI to authenticate users and encrypt traffic. The VPN client on your device will use the public key to encrypt your data so that only the VPN server can decrypt it with their private key. This creates a secure tunnel from your device to the VPN server so that your internet traffic cannot be tracked from its destination back to you.
Key Takeaways
Public Key Infrastructure (PKI) is a framework that manages public key encryption and digital certificates, ensuring secure communication over untrusted networks. It uses a public and private key pair, where the public key encrypts data and the private key decrypts it. These keys are mathematically related but cannot be derived from one another, which makes it safe to give away your public key. If you're struggling to manage your encryption keys, you can use a trusted third party service known as Key Escrow that will help you store your keys. Key escrow can be used for key recovery or compliance but introduces potential security risks.
