1.4 - Hashing & Salting

Learning Objectives
1.4 - Explain the importance of using appropriate cryptographic solutions.
- Hashing
- Salting
What is Hashing?
Hashing is a one-way cryptographic process that converts input data of any size into a fixed-size string of characters, typically of hexadecimal value, known as a hash or message digest.
While encryption focuses on confidentiality, hashing ensures that data has not been altered. This is because even a minor change in input will produce a drastically different output, a property known as the "avalanche effect".
Example:
- Hashing the string "hello" using the SHA-256 algorithm will produce the following hash:
2cf24dba5fb0a30e26e83b2ac5b9e29e1b161e5c1fa7425e73043362938b9824SHA-256 hash value of: "hello"
- However, the string "Hello" with only a change in the capitalisation of a single letter, will produce the following hash while using the same SHA-256 algorithm:
185f8db32271fe25f561a6fc938b2e264306ec304eda518007d1764826381969SHA-256 hash value of: "Hello"
Characteristics of Hashing
- Deterministic: A hash function is deterministic, meaning that the same input will always produce the same hash output.
- Fixed Output Size: Regardless of the input size, a hash function produces a fixed-size output.
- One-Way Function: Hashing is a one-way function, meaning it is computationally infeasible to reverse a hash into its original input.
- Collision Resistance: A good hash function minimises the chances of two different inputs producing the same hash output (a collision).
- Fast Computation: Hash functions are designed to be computationally efficient, allowing for the quick processing of large data.
Common Hashing Algorithms
- MD5 (Message Digest Algorithm 5): Produces a 128-bit hash value and is considered vulnerable due to susceptibility to collision attacks. However, it is still widely used for data integrity checks.
- SHA-1 (Secure Hash Algorithm 1): Produces a 160-bit hash value. Like MD5, it is no longer considered secure due to vulnerabilities.
- SHA-256 (Secure Hash Algorithm 256): Produces a 256-bit hash value and is more secure against collision attacks due to its larger bit size. Currently, no practical vulnerabilities have been discovered, making it widely used for secure hashing requirements.
- SHA-3 (Secure Hash Algorithm 3): Offers variable output sizes (e.g., 256, 512 bits), with a unique unique non-linear structure. It is designed as a ready and compatible replacement if SHA-2 becomes vulnerable.
Use Cases for Hashing
Hashing is used in many real-world applications, too many to explain here, but here are a few common examples:
- Verifying File Integrity: Vendors often provide a hash value for files available to download. Users can hash the downloaded file and compare it to the provided hash to confirm its integrity. If the hash of the received data matches the vendor provided hash, it is guaranteed that the file has not been altered.
- Password Security: Instead of storing plain-text passwords, systems store hashed versions of the passwords. When a user logs in, the system hashes the inputted password and compares it to the stored hash to verify it is correct. This is more secure than storing and transmitting plain-text passwords.
- Unique Identifier: Files or Data can be hashed to create a unique identifier, which allows for easier tracking and management.
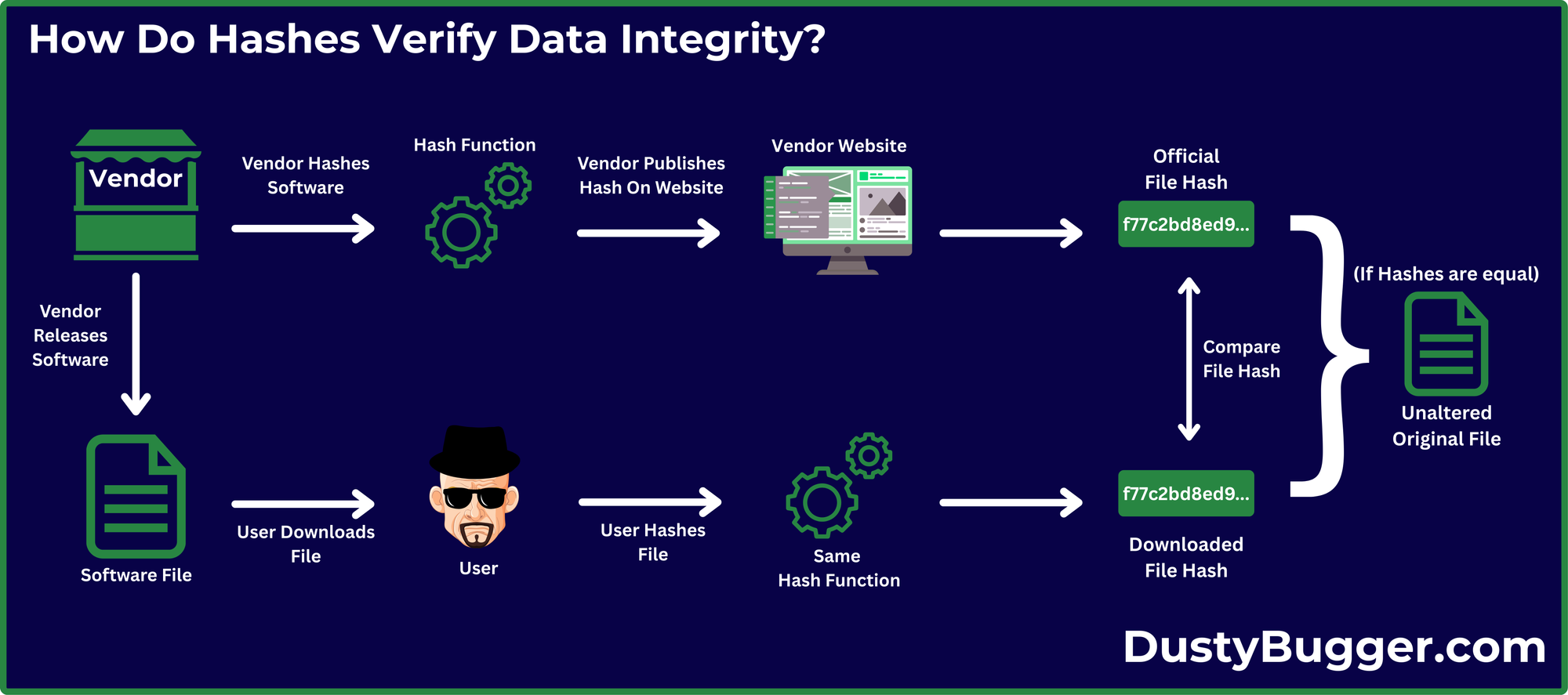
However, it is important to note that hashes alone do not ensure the authenticity of who sent the file. It is possible for malicious actors to imitate an official vendor and provide their own "Official Hash", along with their malicious software to make it seem legitimate. To combat this, we require the use of digital signatures, to ensure authenticity & non-repudiation.
We will cover Digital Signatures in our next lesson, so make sure to subscribe!
What is Salting?
Salting is a technique applied to hashing, particularly in the context of passwords, to protect against attacks like brute forcing or rainbow table attacks.
Salting involves adding random data (known as a "Salt", e.g. "msEVx") to a password or other input before hashing it. This ensures that even if two users have the same plain-text password, their resulting hashes will always be different, as each added Salt is random.
How Does Salting Work In Practice?
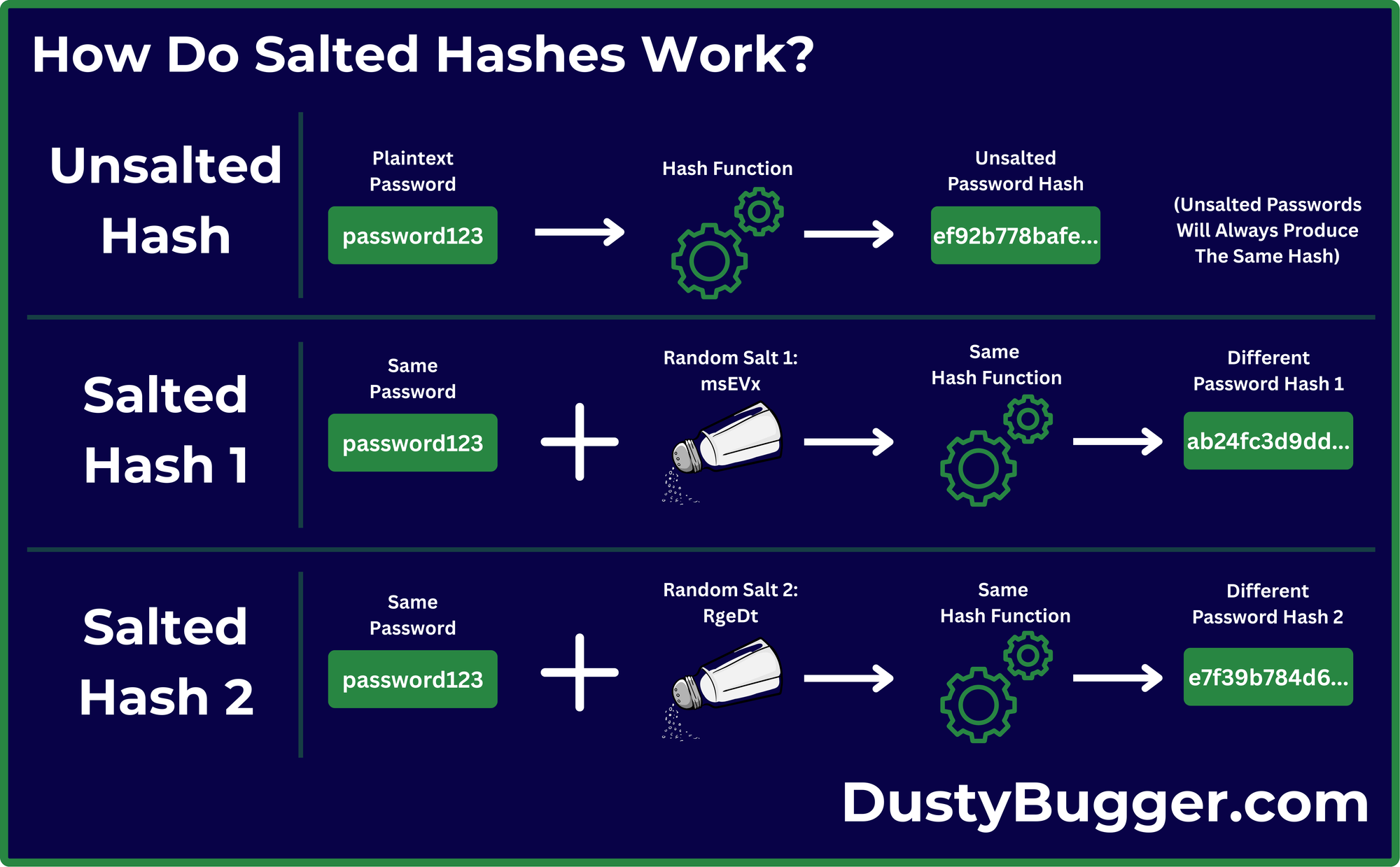
- When a user creates a password, the system generates a random salt and appends it to the password. For example, if the password is "password123" and the random salt is "msEVx", the system hashes "password123msEVx".
- The system then stores the resulting hash along with the salt.
- When the user logs in, the system retrieves the stored salt, adds it to the entered password, and hashes the combined value.
- The system then checks if the generated hash matches the stored hash for that account. If it is a match, then the user is successfully logged in!
Benefits of Salted Hashes
Unique Hashes for Identical Passwords
By adding a random salt to each password before hashing, identical passwords will result in distinct hashes. This prevents attackers from easily identifying common passwords across multiple accounts if password hashes are captured.
Resistance to Rainbow Table Attacks
Salting makes precomputed rainbow tables ineffective because the salt changes the hash output, requiring attackers to generate new tables for each unique salt, significantly increasing computational effort and storage requirements.
Slows Down Brute Force Attacks
Although salting does not stop brute force attempts completely, it significantly increases the complexity and time required to crack each unique hash that an attacker gains access to. This is because for each hash, an attacker will not only have to try every possible password, but also try every possible salt value for each one of those passwords.