1.4 - Digital Signatures

Learning Objectives
1.4 - Explain the importance of using appropriate cryptographic solutions.
- Digital signatures
What are Digital Signatures?
A digital signature is a cryptographic technique used to validate the authenticity and integrity of a digital message or document. It acts as a virtual fingerprint that is unique to the signer, ensuring that the message was sent by the stated sender and remains unaltered during transmission.
Essentially, it combines the integrity verification of Hashing with the authenticity of Public Key Infrastructure, to provide three key assurances:
- Integrity: It ensures that the message has not been altered since the time at which it was signed.
- Authentication: It confirms the identity of the sender, proving the source of the message.
- Non-repudiation: It prevents the sender from denying their involvement in sending the message or other digitally signed actions.
How do Digital Signatures work?
Digital signatures use asymmetric encryption to both sign and verify a piece of data, this is possible due the the mathematical relation between the public-private key pair. A visualisation of this can be seen below:
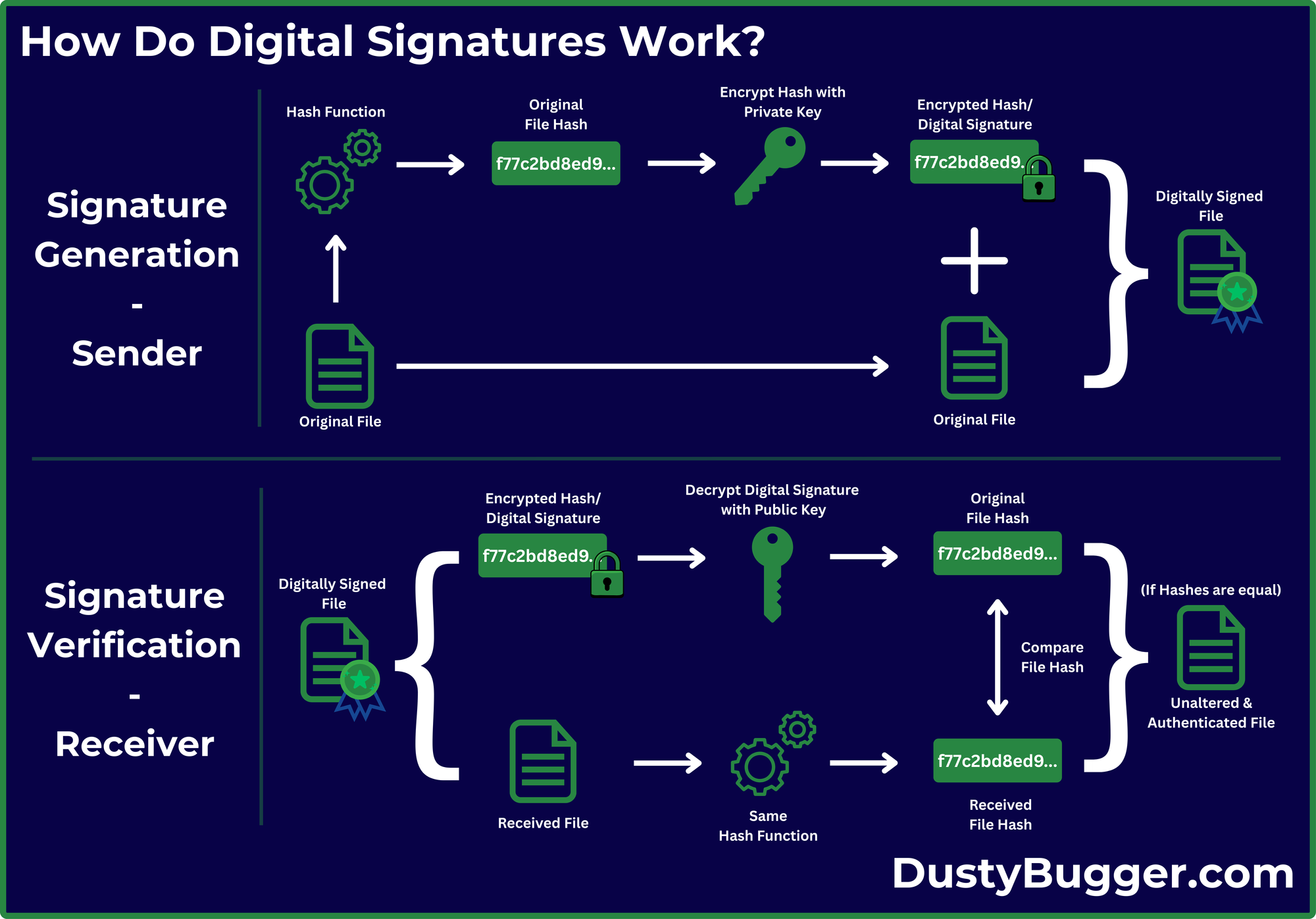
Signing Process - Sender:
The person sending the file is responsible for completing the signing process to authenticate themself and ensure integrity of the file. To do this, they will complete the following steps:
- Sender creates a message digest(hash) of the file by running it through a hash function. For the sake of this explanation, we will refer to this as the "original hash".
- The original file hash is then encrypted using the sender's private key to create a digital signature. This process is known as signature generation, and because it utilises their private key, only the owner can create the signature.
- The sender then attaches the digital signature to the original file and sends it directly to the receiver or makes it available publicly for all to download.
Verification Process - Receiver:
The person receiving or downloading the file, is responsible for completing the verification process to ensure the file has not been altered and that the sender is who they say they are. To do this, they will complete the following steps:
- Receiver uses the sender's public key to decrypt the digital signature and access the sender's original hash.
- The receiver then uses the same hash function on the received file to generate a comparison hash.
- After this, the receiver will compare the hashes to ensure they are the same.
This is known as signature verification and there are three possible outcomes:
- If the original hash and the comparison hash match, then the sender is authentic and the data has not been altered.
- If the original hash and comparison hash do not match, this is proof that the data has been altered.
- If the public key cannot decrypt the digital signature, this proves that the digital signature was replaced with a signature from a different private key. Thus showing a failure in sender authentication.
It is important to note that only in the case of the first result ("1."), is non-repudiation enforced on the sender. If the hashes do not match or the signature cannot be decrypted with the sender's public key, then this is enough evidence for the sender to repudiate(deny) having sent the file or performed such other digitally signed action.
Benefits of Digital Signatures
Digital signatures offer several advantages in maintaining secure communications:
- Fraud Prevention: By ensuring data integrity, sender authentication and non repudiation, digital signatures help to prevent fraud within digital transactions.
- Efficiency and Cost-effectiveness: Digital signatures streamline traditional processes by enabling paperless transactions, reducing the need for physical documentation, and increasing speed and convenience.
- Legal Acceptance: In many jurisdictions, digital signatures are legally recognised, providing legal validity that is equal to or better than handwritten signatures.
Real-world Uses of Digital Signatures
Digital signatures are widely used across various sectors and applications:
- Email Verification: Used to confirm the authenticity of email communications, ensuring that messages come from legitimate sources and have not been altered.
- Software Distribution: Ensures that software and updates are delivered unaltered from the original creator, protecting users from malicious code.
- Financial Transactions: Digital Signatures can secure online banking operations by verifying the identities of involved parties and ensuring the integrity of transactions.
- Legal Documents: Allows for secure signing of electronic contracts and agreements by ensuring the integrity of the documents, authentication of the signing parties, and enforcing non-repudiation to assure they are legally binding.
Weaknesses of Digital Signatures
While Digital Signatures add another layer of security on top of the integrity verification that hashing provides, there is nothing stopping malicious actors from creating their own public-private key pairs and digitally signing their own malicious software in an attempt to imitate an official vendor.
So how do we know if the public key we are using belongs to a legitimate vendor or a malicious imitator? This is where Digital Certificates come in handy. Digital Certificates allow us to trace a public key to the owners true identity through the use of trusted Certificate Authorities.
We will be covering Digital Certificates in our next post, so make sure to subscribe!